
In the realm of software development, efficiency is the name of the game.
Every developer knows the frustration of dealing with networking issues, especially when it comes to accessing remote resources securely. Fortunately, there’s a powerful tool at your disposal that can revolutionize the way you work: SSH port forwarding.
SSH (Secure Shell) port forwarding, also known as SSH tunneling, is a technique that allows you to securely transmit data across the internet, bypass firewalls, and access resources on remote servers as if they were local. While it may sound like a niche skill, mastering SSH port forwarding can significantly boost your development productivity in various ways.
Let’s look at a few scenarios and how to leverage SSH tunneling to solve them.
1. Local Port Forwarding
Imagine you’re working on a project that involves accessing a remote PSQL database for development and testing purposes. However, the database server is only accessible from within the organisation’s network due to security restrictions.
How can you access the database securely from outside of the organisation?
Connecting to your organisation laptop with SSH and creating a tunnel that redirects the traffic to the database server port, which the organisation server has access to. Use the following ssh command:
$> ssh -f -N dev@org_laptop_ip -L 5432:psql_server_ip:5432
-f: Requests ssh to go to background just before command execution.
-N: Do not execute a remote command.
-L: Specify local port

You can now connect to the database locally @ 127.0.0.1:5432.
2. Remote Port Forwarding
Imagine you’re working on a project and need to access a debugging interface running on a specific port (let’s say port 9999) on the development server to troubleshoot an issue. However, the debugging interface is only listening on 127.0.0.1.
How can you access securely the debug interface from your local machine?
Connecting to the debug server SSH port, creating a tunnel and port forward the remote debug port into your local machine, with the following command:
$> ssh -f -N dev@debug_server -R 9999:localhost:9999
-f: Requests ssh to go to background just before command execution.
-N: Do not execute a remote command.
-R: Specify remote port

You can now connect to the debugging interface locally @ 127.0.0.1:9999.
3. Dynamic Port Forwarding
Imagine you’re a software developer attending a tech conference where the venue’s Wi-Fi network has restricted access to certain websites and services. However, you need to access these resources for research and communication during the conference.
How can you access freely to these resources?
Establishing an SSH tunnel that listens on a specific local port (such as 1080) and supports both SOCKS4 and SOCKS5 protocols, enabling unrestricted access the web despite limitations imposed by the conference’s Wi-Fi network. This tunnel securely proxies all traffic to the remote server, which can then relay traffic to the internet. Use the following command:
$> ssh -f -N -D 1080 dev@remote_server
-f: Requests ssh to go to background just before command execution.
-N: Do not execute a remote command.
-D: Specifies a local “dynamic” application-level port forwarding.
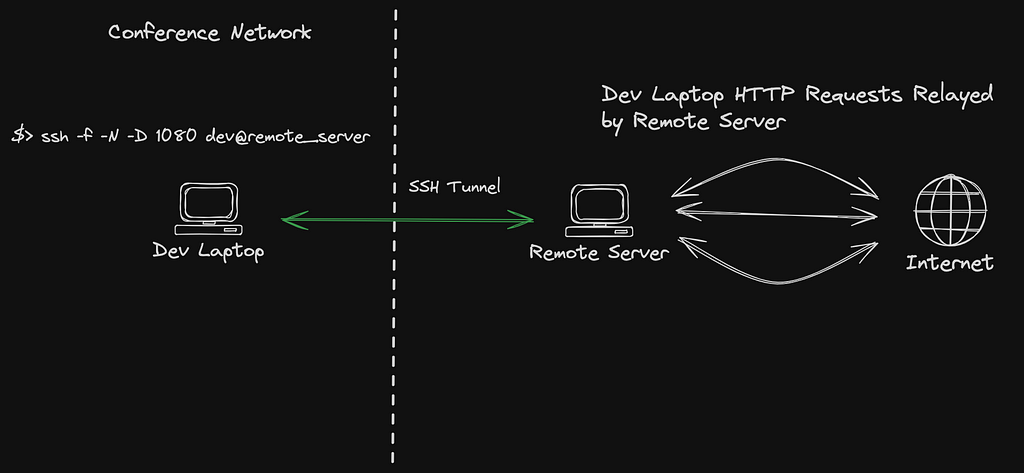
You can now browse the internet freely, by proxying traffic @ 127.0.0.1:1080.
Conclusion
Whenever you finish the task, it is good practice to close the SSH tunnels. Issue the following command to close all ongoing SSH connections on your machine:
$> pkill ssh
These SSH tricks might save you loads of hassle when configuring your local development environment or even on some edge cases that you might encounter on your daily work. Make sure to use them to your advantage!